Hikvision SADP is a useful tool which allows to control and active NVR devices within a local network. Unfortunately it is not so useful when dealing with remote devices.
Although there is a small trick. SADP uses a multicast address 239.255.255.230 and a UDP port 37020 for sending and receiving control packets to/from Hikvision devices. This info can be used to create a listening socket on a device within the same network as a host running SADP that will forward these packets to remote networks without setting up multicast routing.
Let’s consider the following topology for our example:
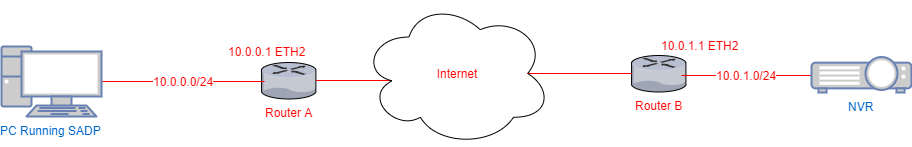
We can create a TCP tunnel over SSH and use it to send out multicast requests to the necessary subnet behind Router B. To accomplish this we would need to:
1. Setup an SSH tunnel from Router A to Router B with local Port binding:
ssh user@routerB -L 0.0.0.0:7999:127.0.0.1:7999
2. Setup a local UDP multicast receiver on Router A with forward to the TCP tunnel:
socat -T15 udp4-recvfrom:37020,ip-add-membership=239.255.255.250:10.0.0.1,reuseaddr,fork tcp:localhost:7999
3. Setup a TCP receiver with forward to UDP multicast on Router B
socat tcp4-listen:7999,reuseaddr,fork udp4-datagram:239.255.255.250:37020,bind=:37020,ip-add-membership=239.255.255.250:eth2,sourceport=:37020,bindtodevice=eth2
Notes:
1. If you are using firewalls, we need to setup rules for Multicast and port listening. An example for IPTABLES:
iptables -I INPUT -p udp –dport 37020
iptables -I INPUT -p tcp –dport 7999
iptables -I INPUT -d 224.0.0.0/4 -j ACCEPT
iptables -I INPUT -s 224.0.0.0/4 -j ACCEPT
2. We also would need to setup a multicast route for Router B, so traffic gets sent to the appropriate interface.
route add 239.255.255.250/32 eth2